Security Certificates Workspace
When you click the Certificate node in the SMC tree, you can create Windows-store based and file based certificates using the toolbar controls.
Once created, the Windows-store based certificates must be imported in the Windows Certificate store for using them as default certificates in various SMC workflows. You can do this using the Default Certificates expander.
Create Certificate
Use Create Certificate  to create any of the following certificates. For the very first time, most of the fields are blank.
to create any of the following certificates. For the very first time, most of the fields are blank.
For all subsequent root/host certificates you create, some fields, such as Path or Organization are pre-populated with information from the last-created root certificate.
When you click Create Certificate > Create Root Certificate (.pem), the Root Certificate Information expander displays. It allows you to create a .pem root certificate.
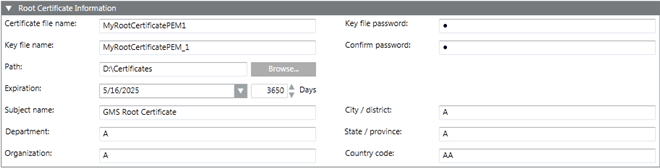
Root Certificate Information Expander | |
| Description |
Certificate file name | Type the file name of the root certificate. The certificate and the key file name should not contain blanks for special characters (/,\,?,<, >,*,|,"). |
Key file name | Type the key file name. |
Key file password | Type the password required to secure the root key file. This password is required for creating host certificates. |
Confirm password | Re-enter the password for confirmation. |
Path | Browse for the location to store the certificate on the disk. |
Expiration | Set the validity period. Once a certificate's validity period is over, a new certificate must be requested by the subject of the now-expired certificate. By default, the certificate expires after 3650 days. |
Subject Identifier Information | Provide the subject's identifier information: |
When you click Create Certificate > Create Host Certificate (.pem), the Host Certificate Information expander displays. This allows you to create a .pem host certificate.
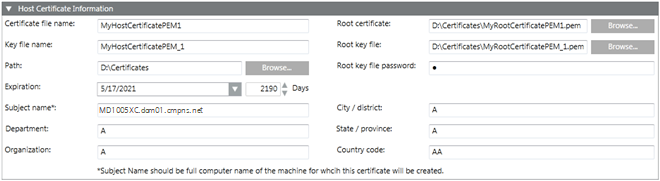
Host Certificate Information Expander | |
| Description |
Certificate file name | Type the file name of the host certificate. The certificate and the key file name must not contain blanks and special characters (/,\,?,<, >,*,|,"). |
Key file name | Type the key file name. The certificate and the key file name should not contain blanks and special characters (/,\,?,<, >,*,|,"). |
Path | Browse for the location to store the certificate on the disk. By default, the path of the last created root certificate is selected. |
Expiration | Set the validity period for the host certificate. Once a certificate's validity period is over, a new certificate must be requested by the subject of the now-expired certificate. By default, the certificate expires after 2190 days. |
Root certificate | Browse for the root certificate. By default, the last created root certificate is selected. |
Root key file | Browse for the root key file. By default, the last created root key file is selected. |
Root key file password | Type the password for the selected root key file. |
Subject Identifier Information | Allows you to provide the subject's identifier information: |
When you click Create Certificate > Create Root Certificate (.pfx), the Root Certificate Information expander displays. This allows you to create a .pfx root certificate.
You need a root certificate (.pfx file) to create a host certificate (.pfx file). You can create multiple host certificates using one root certificate (.pfx file).
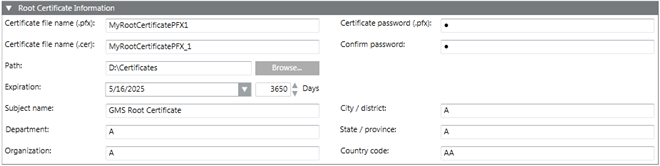
Root Certificate Information Expander | |
| Description |
Certificate file name (.pfx) | Type the file name of the root certificate with .pfx extension. You can use this file to create a host certificate (.pfx). The certificate file name must not contain blanks and special characters (/,\,?,<, >,*,|,"). |
Certificate file name (.cer) | Type the file name of the .cer root certificate. Note that the .pfx file contains both key and certificate; however, the .cer certificate file contains only the certificate. You must then import this .cer certificate file in the Windows store on the client/FEP for establishing a secure communication between server and clients. The certificate file name must not contain blanks or special characters (/,\,?,<, >,*,|,"). |
Certificate password (.pfx) | Type the password required to secure the certificate. This password is required for creating host certificates. |
Confirm password | Re-enter the password. |
Path | Browse for the location to store the certificate on the disk. |
Expiration | Set the validity period. Once a certificate's validity period is over, a new certificate must be requested by the subject of the now-expired certificate. By default, the certificate expires after 3650 days. |
Subject Identifier Information | Provide the subject's identifier information: |
When you click Create Certificate > Create Host Certificate (.pfx), the Host Certificate Information expander displays. This allows you to create a .pfx host certificate. Note that this creates two host certificates; one with the extension .pfx and another with the extension .cer, at the specified location on the disk.
In order to create a .pfx host certificate, you must have a .pfx root certificate. You can create multiple host certificates using one .pfx root certificate.
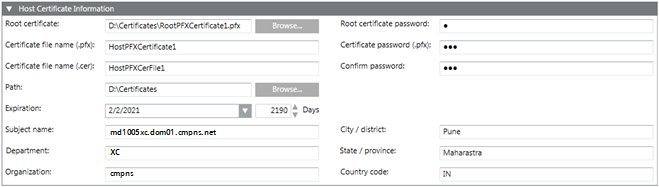
Host Certificate Information Expander | |
| Description |
Root certificate | Browse for the .pfx root certificate. By default, the last created .pfx root certificate is selected. |
Root certificate password | Type the password for the selected root certificate. |
Certificate file name (.pfx) | Type the .pfx file name of the host certificate. |
Certificate password (.pfx) | Type the valid password for the certificate. |
Confirm password | Re-enter the certificate password. |
Certificate file name (.cer) | Type the .cer file name of the host certificate. |
Path | Browse for the location to store the certificate on the disk. By default, the path of the last created root certificate is selected. |
Expiration | Set the validity period for the host certificate. Once a certificate's validity period is over, a new certificate must be requested by the subject of the now-expired certificate. By default, the certificate expires after 2190 days. |
Subject Identifier Information | Provide the subject's identifier information: |
When you click Create Certificate > Create Self-Signed Certificate (.pfx), the Self-Signed Certificate Information expander displays. This allows you to create a .pfx self-signed certificate. Once you set the self-signed certificate as default, during website and web application creation, it displays in the Certificate issued to field of the Details and Web application Details expander respectively.
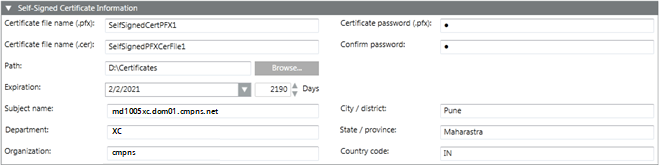
Self-Signed Certificate Information Expander | |
Name | Description |
Certificate file name (.pfx) | Type the file name of the .pfx self-signed certificate. The certificate file name must not contain blanks or special characters (/,\,?,<, >,*,|,"). |
Certificate file name (.cer) | Type the file name of the self-signed certificate with .cer extension. Note that the .pfx file contains both key and certificate; however, the .cer certificate file contains only the certificate. The certificate file name must not contain blanks or special characters (/,\,?,<, >,*,|,"). |
Certificate password (.pfx) | Type the password required to secure the certificate. |
Confirm password | Re-enter the password. |
Path | Browse for the location to store the certificate on the disk. |
Expiration | Set the validity period. Once a certificate's validity period is over, a new certificate must be requested by the subject of the now-expired certificate. By default, the certificate expires after 2190 days. |
Subject Identifier Information | Allows you to provide the subject's identifier information:
|
Validity of Self-Signed Certificates
Self-signed certificates allow local deployments without the overhead of obtaining commercial certificates. When using self-signed certificates, the owner of the Desigo CC system is responsible for maintaining their validity status, and for manually adding them to and removing them from the list of trusted certificates.
Self-signed certificates must only be used in accordance with local IT regulations (several CIO organizations do not allow them, and network scans will identify them). Importing the commercial certificates follows the same procedures.
You must ensure the compliant installation of the trusted material on the involved machines, for example, on all Installed Clients. In some organizations, this must be done by the IT organization.
Import Certificate
Use Import Certificate  to import the Windows store certificate types (root, host, and self-signed) in the Windows Certificate store.
to import the Windows store certificate types (root, host, and self-signed) in the Windows Certificate store.
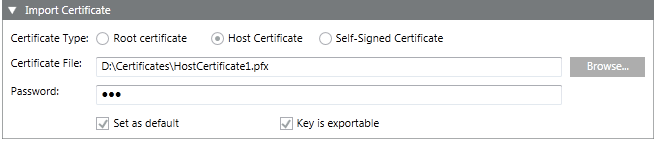
When you click Import Certificate  , the Import Certificate expander displays. It allows you to select a root, host or self-signed certificate from the specified location on the disk and import it in the appropriate Windows store.
, the Import Certificate expander displays. It allows you to select a root, host or self-signed certificate from the specified location on the disk and import it in the appropriate Windows store.

NOTE:
Only import certificates obtained from trusted sources. Importing an unreliable certificate can compromise the security of any system component that uses the imported certificate.
The following table displays Import Certificate expander fields.
Field | Description |
Certificate Type | Allows you to select a root, host (default selection) or self-signed certificate types for importing. |
Certificate File | Allows you to browse and navigate to a certificate file for the selected certificate type on the disk. To import |
Password | Enter the password of the selected certificate file (not applicable for the root certificate). |
Set as Default | When selected, allows you to set the selected certificate type as default. Once you select the Set as Default check box, the default certificates display by default in the Default Certificates expander. |
Key is exportable | Allows you to back up or transport your keys at a later time. The host certificate that is used for secured client/server communication must have the Key as exportable check box selected. |
For information on where the certificates are imported in the Windows Certificate store location (Personal or Trusted Root Certification Authorities), see Certificate Store. You can verify this from Microsoft Management Console (MMC 3.0).
Default Certificates
Click Edit  to set or modify the default (root, host, or self-signed) certificates, view details, and clear the default certificates.
to set or modify the default (root, host, or self-signed) certificates, view details, and clear the default certificates.
It helps you to browse, select and set the default root, host and self-signed certificates from the Windows Certificate store.
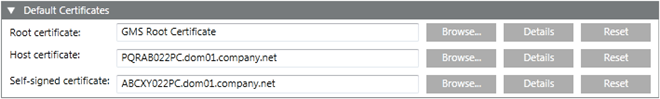
- Root Certificate: Allows you to browse (when you click Browse) and select a root certificate already imported in the Store location - Local machine certificates > Trusted Root Certification Authorities.
- Host certificate: Allows you to browse and select a host certificate already imported in the Store location - Local machine certificates > Personal.
- Self-Signed certificate: Allows you to browse and select a self-signed certificate already imported in the Store location - Local machine certificates > Personal.
- Details: Click Details to view the certificate details.
- Reset: Click Reset when you want to clear the default certificate.
The default certificate, that are not available in the Windows Certificate store are indicated in red in the Default Certificate expander.

NOTE:
You cannot set a CNG certificate with ECDSA signature algorithm as a default root or host certificate.
The following table describes the default certificates and the location where they display by default in the SMC.
Default Certificate Type | Displays as the Default Certificate in the Field… |
Root | Root Certificate of the Communication Security expander, when you modify the Server project (using the Server Communication section) or modify Client/FEP project (using the Server communication section) and the client server communication type is Secured and no certificates are configured. |
Host | Host Certificate of the Communication Security expander, when you modify the Server project (using the Server Communication section) or modify Client/FEP project (using the Server communication section) and the client server communication type is Secured and no certificates are configured |
Self-signed | Certificate issued to field of the Details expander when you create the website and |

NOTE:
Only when the self-signed certificate is not set as default, the Create button is enabled in the Details expander when you create a new web site. You can create a new self-signed certificate when you click Create which gets set as default self-signed certificate for web site/web application.
