OpenID Connect for Flex Client Authentication
The OpenID user login is a decentralized authentication system for the Desigo CC Flex Client. It ensures a secure authentication on the Desigo CC Flex Client on projects that do not have their own domain infrastructure. If you already use OpenID as the authentication system, you can also use the existing Identity Provider account in Desigo CC.
The authentication is managed by one of the supported Identity Access Management platforms (IAM). See Supported Identity and Access Management Platforms.
For configuration instructions in Desigo CC, see Create a New Local OpenID User for Flex Client.

NOTE:
If the user is working with Flex Client and the Desigo CC client, a separate Desigo CC user must be set up for the Desigo CC client.
You must request credentials from the OpenID provider to login with an OpenID user login; the credentials must be entered in Desigo CC in the Identity Provider tab.
- Register the project with the OpenID provider and publish the redirect URL from the Desigo CC Web Service Interface.
- You receive a domain address from the identity provider, a client ID as well as a client secret key ID. This information must be entered in the Identity Provider Configuration tab.
- Each Desigo CC user in the project must register using his or her e-mail address and a password with the identity provider with an account.
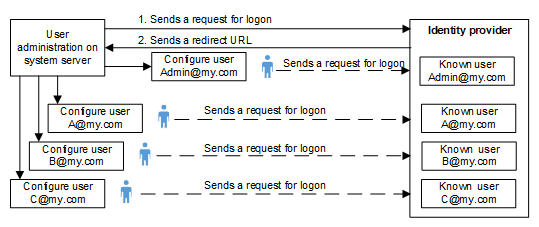
See also the configuration example in Auth0 OpenID Configuration Example.
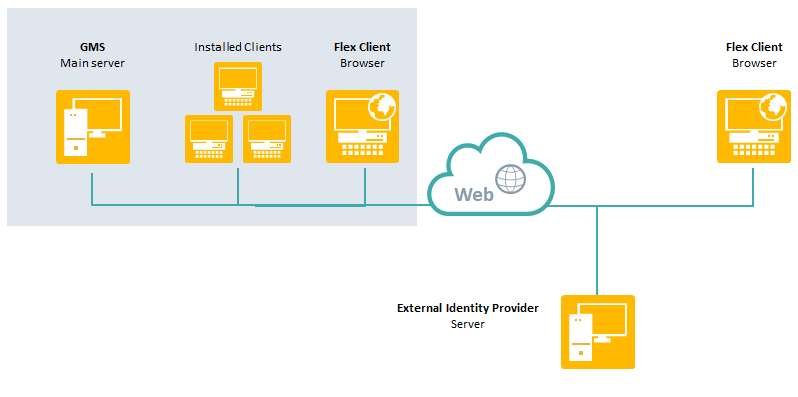
A Flex Client user can login to Desigo CC both within and outside the project network with the OpenID. The OpenID cannot be used as the user login on the Desigo CC client. This request another Desigo CC user account.
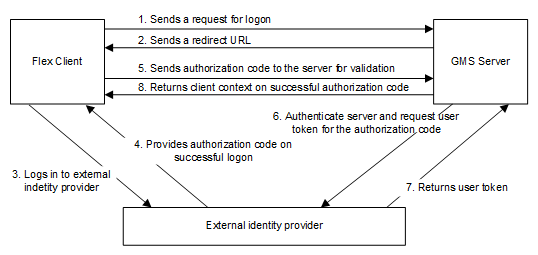
If an OpenID is entered on a Desigo CC user account, authentication of a Desigo CC Flex Client login is an eight-step process. The ID token authentication process includes the corresponding ID data and the information is transmitted in encrypted form via the https protocol. Only authorization code flow is supported for login. All other authorization procedures are not supported in Desigo CC.
In the Identity Provider tab of the Users node, you can configure the Open ID settings.
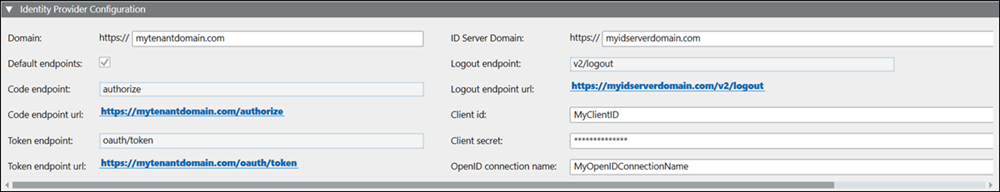
OpenID Configuration | |
Entry field | Description |
Domain | Enter the domain address for the identity provider, for example, abc.def.xyz. |
Default endpoints | If the check box is cleared, you can enter specific data under Code endpoint and Token endpoint. |
Code endpoint | Enter the data for the identity provider if the code endpoint is different from the standard code endpoint (authorize). |
Code endpoint url | The Code endpoint URL is a combination of Domain and Code endpoint. |
Token endpoint | Enter the data for the identity provider if the token endpoint is different from the standard token endpoint (oauth/token). |
Token endpoint url | The Token endpoint URL is a combination of Domain and Token endpoint. |
ID Server Domain | Enter the ID Server domain for the identity provider, for example, abc.def.xyz |
Logout endpoint | Enter the data for the identity provider if the logout endpoint is different from the standard logout endpoint (v2/logout). |
Logout endpoint url | Logout endpoint URL is the URL that is formed as a combination of ID Server domain and Logout endpoint. This URL is used to submit logout request to the OpenID server. |
Client ID | It is a unique ID supplied by the identity provider or must be requested from the provider. Each user receives its own assigned ID. |
Client secret | It is a unique ID supplied by the identity provider together with the client ID. |
OpenID connection name | This is the connection name of the Authorization server added to the IAM platform. Connection name helps in directly navigating to the authentication page of the server. In case this field is kept empty, a standard Auth0 page is displayed where you will have to select connection from the list of connections available on the IAM platform. |
