Domain Groups
Scenario: Existing IT infrastructure that includes domain groups can be used for the user administration in Desigo CC . After selecting the domain, domain groups can be assigned to Desigo CC user groups.
Reference: For general information on domain groups (LDAP), see the reference section User Group Administration chapter Domain Groups LDAP.
Workflow diagram:
Prerequisites:
- System Manager is in Engineering mode.
- System Browser is in Management View.
Steps:
Scenario: The domain configuration must be set up once to get access to the domain groups. It supports one domain server only.
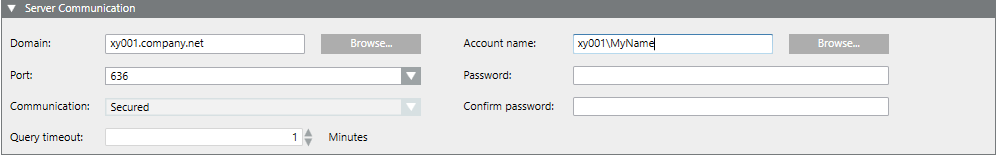
- Select Project > System Settings > Security.
- Select the LDAP tab and open the Server Communication expander.
- Enter the domain name in the Domain field, for example, xy001.company.net or click Browse to find the desired domain name.
- From the Port drop-down-list, select:
- 636 for secure connection
- 389 for unsecured connection or
- enter a port number and from the Communication drop-down-list, select Secured or Unsecured connection.
- In the Account name field, enter the account name, for example, xy001\MyName or click Browse to find the desired user name.
NOTES:
This functional user only needs to have restricted rights with read access on groups, group membership and users in the directory server.
This functional user should have a password without an expiration date. If this is not possible, enter a user account with a password that will expire in a long time. This is because the account will no longer work if the user password is expired.
- In the Password field, enter the password.
- In the Confirm password field, confirm the password.
- In the Query timeout field, enter the number of minutes (from 1 to 60) of timeout inactivity after which an information message will display (Default = 1 minute). In case of a timeout, click OK to continue.
- Click Save
 .
.
- Click Check connection
 .
.
- A message displays.
- OK: Add domain groups to the Group Mapping expander.
- Error: Check the settings for the domain name, port number and account name.
- Click OK.
- A connection to the domain server is established.
- Select Project > System Settings > Security.
- (Optional) Manual assignment procedure:
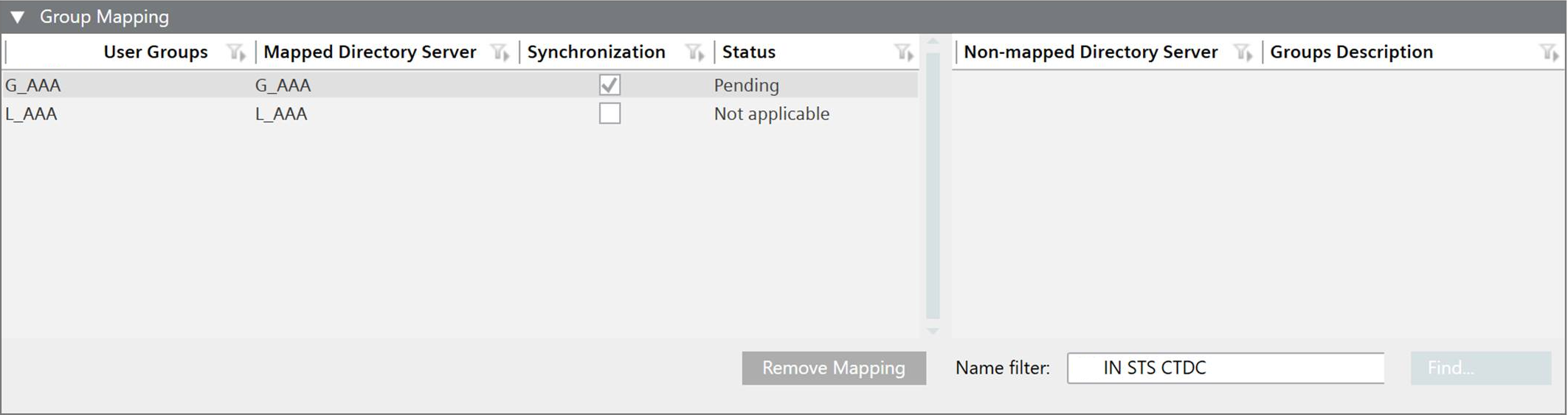
a. Select the LDAP tab and open the Group Mapping expander.
b. In the Name filter field, enter a group name. You can use an asterisk (*) as a wild card at the end of the filter name, for example, CH DEV1*. In a large system, avoid using an asterisk at the beginning of the search phrase because it can result in excessive search times.
c. Click Find.
The groups display in the Non-mapped Directory Server Groups list.
d. Note down the name of the domain group that you want to assign. You will have to enter it in step 6.
- Select the Security tab.
- Click New
 .
.
- In the New Group dialog box:
a. In the Group type field, select User.
b. In the Distribution field, select Global or Local.
c. Enter the group name of the domain group:
- when the assignment is performed manually, the name must be identical with that of the domain group.
- when the assignment is performed via drag-and-drop, you can choose any unique name.
d. Click OK.
- Click Save
 .
.

- A user group exists and is configured.
NOTE: For each used domain group, a Desigo CC user group must exist.
- A connection to the domain server is established.
- Select Project > System Settings > Security.
- Select the LDAP tab and open the Group Mapping expander.
- Enter a group name in the Name filter field. You can use an asterisk (*) as a wild card at the end of the filter name, for example, CH DEV1*. In a large system, avoid using an asterisk at the beginning of the search phrase because it can result in excessive search times.
- Click Find.
- The groups display in the Non-mapped Directory Server Groups list.
- Do one of the following:
- To select via drag-and-drop, do the following:
a. Select a group from the Non-mapped Directory Server Groups list.
b. Drag it onto the Mapped Directory Server Groups list.
NOTE: If a group is already assigned, you can assign a new group by replacing the existing group or cancel the assign operation.
c. Select the Synchronization check box. The Status changes toPending.
d. Click Save .
.
- To select manually, do the following:
a. Select the name in the Desigo CC User Groups column which matches the Mapped Directory Server Groups.
b. Select the name in the Mapped Directory Server Groups list.
c. Select the Synchronization check box. The Status changes toPending.
d. Click Save .
.
- (Optional) Remove an assigned group by clicking Remove Mapping.
- Click Synchronize
 .
.
- The Status changes to
Succeeded.
- All users of that group are assigned to and enabled in the Group Configuration expander of the Security tab.
- Repeat steps 4 to 7 for the other required domain groups.

- A global user group exists and is configured.
NOTE: For each used domain group, a Desigo CC global user group must exist.
- A connection to the domain server is established.
- In the master project, select Project > System Settings > Security.
- Select the LDAP tab and open the Group Mapping expander.
- Enter a group name in the Name filter field. You can use an asterisk (*) as a wild card at the end of the filter name, for example, CH DEV1*. In a large system, avoid using an asterisk at the beginning of the search phrase because it can result in excessive search times.
- Click Find.
- The groups display in the Non-mapped Directory Server Groups list.
- Do one of the following:
- To select via drag-and-drop, do the following:
a. Select a group from the Non-mapped Directory Server Groups list.
b. Drag it onto the Mapped Directory Server Groups list.
NOTE: If a group is already assigned, you can assign a new group by replacing the existing group or cancelling the assign operation.
c. Select the Synchronization check box. The Status changes toPending.
d. Click Save .
.
- To select manually, do the following:
a. Select the name in the Desigo CC User Groups column which matches the Mapped Directory Server Groups.
b. Select the name in the Mapped Directory Server Groups list.
c. Select the Synchronization check box: The Status changes toPending.
d. Click Save .
.
- (Optional) Remove an assigned group by clicking Remove Mapping.
- Click Synchronize
 .
.
- The Status changes to
Succeeded.
- All users of that group are assigned to and enabled in the Group Configuration expander of the Security tab.
- Repeat steps 4 to 7 for the other required domain groups.

NOTE:
If a local account is part of a global group that gets synchronized, this account needs to get promoted to global. As a result, this account’s memberships in all local groups expires, so that it can only be assigned to global groups.
When synchronizing a local group which has an existing global account as member, this membership is ignored and the global account is not added to the local group.
- Users of a domain group are enabled by default.
- Select Project > System Settings > Users.
- Click the Users tab.
- In the Users list, select a user.
- Make the desired changes to the settings for the user.
NOTE: The domain group synchronization does not automatically enable users whose Enabled check box was cleared.
- Click Save
 .
.
- The user is modified.
- Select Project > System Settings > Security.
- In the Extended Operation tab, select the LDAP Synchonization property.
- Click Enable.
- (Optional) Click Synchronize.
NOTE: This feature can only be carried out when the domain groups are defined.
Scenario: A synchronization has to be triggered whenever a user has been added to or removed from a domain group. Depending on the frequency of organizational changes, an automatic synchronization has to be triggered on a daily (weekly or monthly) basis. If a user needs to be added before the automatic synchronization takes place, you need to trigger a manual synchronization.
- Synchronization is enabled.
- Select Applications > Logics > Reactions.
- The Reaction Editor tab displays.
- Open the General Settings expander.
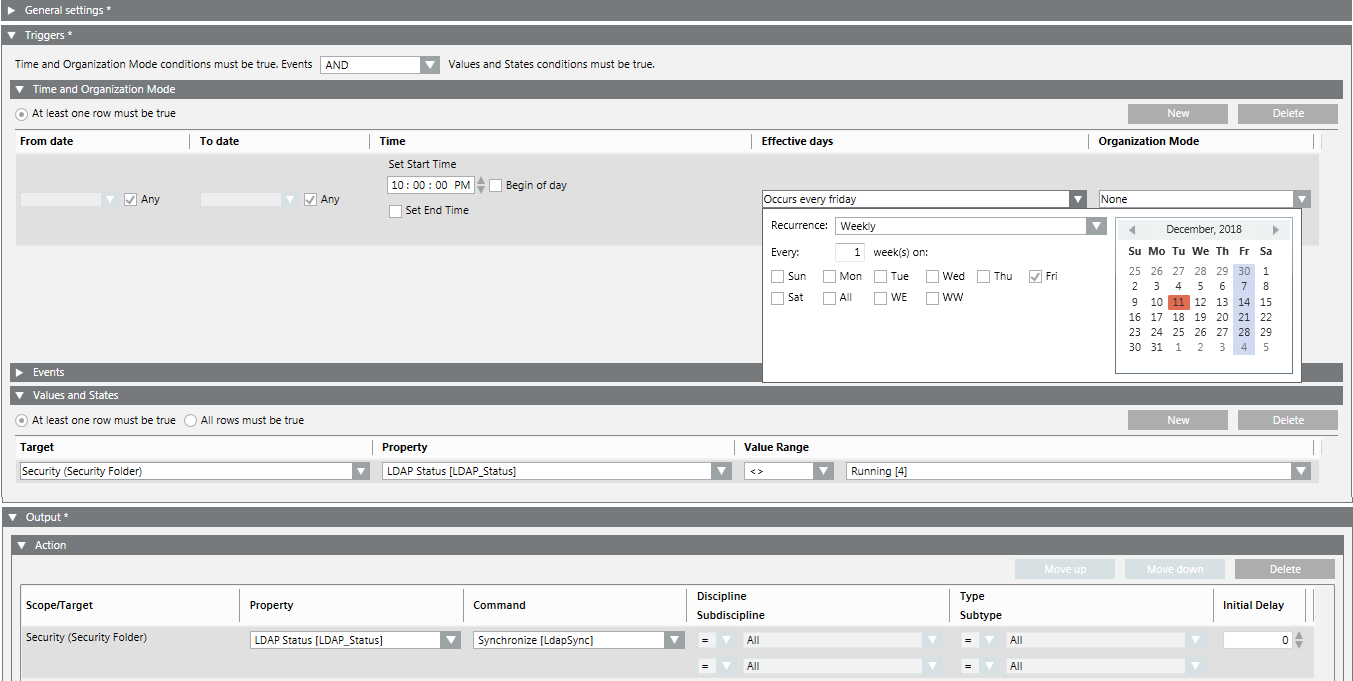
- In the Notes field, enter Automatic synchronization of LDAP every night at 10 PM.
- In the Triggers expander, select from the drop-down-list the condition AND.
- In the Time and Organization Mode expander, set its fields as follows:
a. In the Time column, clear the Begin of day check box, in the Set start time field enter 10:00:00 PM.
b. Clear the Set end time check box.
c. In the Effective Days column, open the drop-down list and, for example, set Recurrence: Weekly, select the frequency Every: 1 week, and select an option.
- In the Output expander, open the Action expander.
a. In System Browser, select Management View.
b. Select Project > System Settings > Security.
c. Drag Security into the empty area of the Scope/Target column in the Action expander.
d. In the Property column, select LDAP Status.
e. In the Command column, select Synchronize.
f. In the remaining four fields, leave the default setting (All).
- (Optional) In the Triggers expander, open the Values and States expander.
NOTE: This setting avoids an additional run if the synchronization is already running.
a. Select Project > System Settings > Security.
b. Drag Security into the empty area of the Target column in the Values and States expander.
c. In the Property column, select LDAP Status.
d. In the Value Range column, select <> and Running.
e. Select the At least one row must be true option.
- Click Save As
 .
.
- In the Save Object As dialog box, select the main Reactions folder or any subfolder under it as the saving destination:
a. Enter name and description, for example, Automatic Daily LDAP Synchronization.
b. Click OK.
- The new reaction object is available in System Browser, and is enabled by default.
- The execution of the LDAP synchronization is logged. In case of a synchronization error, a status alarm is triggered.